In the evolving landscape of blockchain technology, privacy has emerged as one of the most critical challenges facing decentralized networks. While blockchain's transparent nature provides unprecedented accountability and trust, it also exposes transaction details and user behaviors to public scrutiny. Privacy-preserving technologies represent a sophisticated solution to this paradox, enabling confidential transactions while maintaining the integrity and transparency that make blockchain revolutionary.

Visualization of privacy-preserving blockchain architecture
The Privacy Challenge in Decentralized Systems
Traditional blockchain networks operate on a principle of radical transparency. Every transaction, from the smallest transfer to major smart contract executions, is recorded on a public ledger accessible to anyone. While this transparency ensures accountability and prevents double-spending, it creates significant privacy concerns for individuals and organizations alike.
Consider a business conducting transactions on a public blockchain. Competitors could analyze transaction patterns, identify suppliers, estimate revenues, and gain strategic insights that would normally remain confidential. Similarly, individuals face risks of financial surveillance, where their entire transaction history becomes permanently accessible to anyone with basic blockchain analysis tools.
Key Privacy Concerns
- Transaction linkability:The ability to connect multiple transactions to a single user
- Address clustering:Techniques that group addresses belonging to the same entity
- Amount visibility:Public exposure of transaction values
- Metadata leakage:Timing and pattern analysis revealing user behavior
Zero-Knowledge Proofs: Proving Without Revealing
Zero-knowledge proofs (ZKPs) represent one of the most elegant solutions to blockchain privacy. These cryptographic protocols allow one party to prove to another that a statement is true without revealing any information beyond the validity of the statement itself. In the context of blockchain, this means proving you have sufficient funds for a transaction without revealing your actual balance or transaction history.
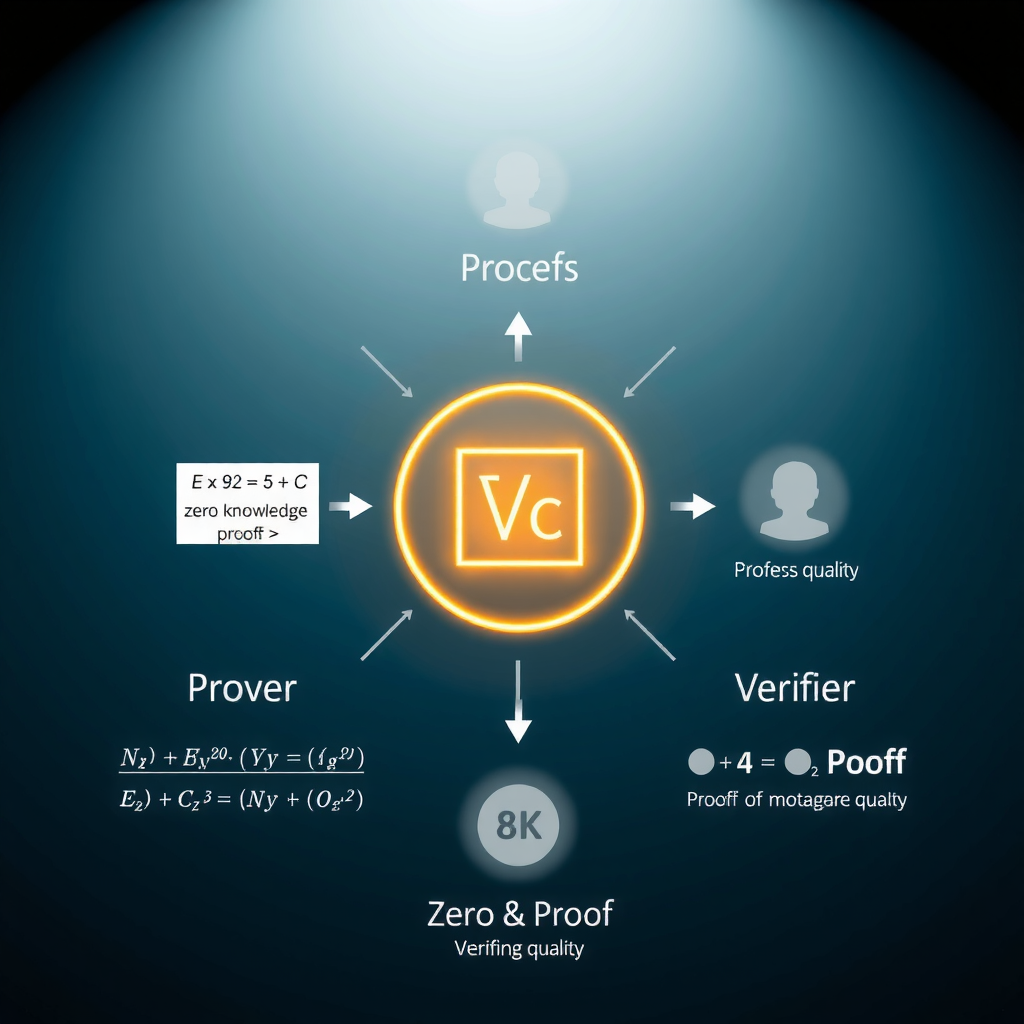
How zero-knowledge proofs enable verification without disclosure
zk-SNARKs: Succinct Non-Interactive Arguments
Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge, orzk-SNARKs, have become the foundation for several privacy-focused blockchain implementations. These proofs are "succinct" because they're small and fast to verify, and "non-interactive" because they don't require back-and-forth communication between prover and verifier.
The innovation of zk-SNARKs lies in their ability to compress complex computational statements into tiny proofs. A transaction involving thousands of inputs and outputs can be verified with a proof of just a few hundred bytes, processed in milliseconds. This efficiency makes zk-SNARKs practical for blockchain applications where every byte of data and every millisecond of processing time matters.
"Zero-knowledge proofs represent a fundamental shift in how we think about verification. Instead of showing all our cards to prove we have a winning hand, we can prove we're winners without revealing a single card."
zk-STARKs: Transparent and Scalable
Zero-Knowledge Scalable Transparent Arguments of Knowledge, orzk-STARKs, offer an alternative approach that addresses some limitations of zk-SNARKs. The key advantage of zk-STARKs is their transparency—they don't require a trusted setup ceremony, eliminating a potential security vulnerability. They're also believed to be quantum-resistant, providing long-term security as quantum computing advances.
While zk-STARKs generate larger proofs than zk-SNARKs, their verification time scales logarithmically with computational complexity, making them increasingly attractive for complex applications. Several blockchain projects are exploring zk-STARKs for scaling solutions that also enhance privacy.
Ring Signatures: Hiding in the Crowd
Ring signatures provide a different approach to blockchain privacy by obscuring the true signer of a transaction within a group of possible signers. Imagine a document signed by someone in a group of ten people—you know one of them signed it, but you can't determine which one. This is the essence of ring signatures in blockchain technology.

Ring signatures create plausible deniability by mixing transactions
How Ring Signatures Work
When a user creates a transaction using ring signatures, they select several other public keys from the blockchain to form a "ring" with their own key. The cryptographic signature proves that someone in the ring authorized the transaction, but it's computationally impossible to determine which specific member signed it. This creates plausible deniability for all ring members.
The size of the ring directly impacts privacy—larger rings provide better anonymity but require more computational resources and blockchain space. Modern implementations use ring sizes of 11 or more, providing strong privacy guarantees while maintaining reasonable efficiency.
Stealth Addresses: Unlinkable Destinations
Ring signatures are often combined with stealth addresses to provide comprehensive transaction privacy. Stealth addresses ensure that even if someone knows your public address, they cannot determine which transactions on the blockchain are sent to you. Each transaction creates a unique, one-time destination address that only you can recognize and spend from.
This combination of ring signatures and stealth addresses creates a powerful privacy system where neither the sender, receiver, nor transaction amount can be easily determined by blockchain observers. This technology forms the foundation of several privacy-focused cryptocurrencies.
Confidential Transactions: Hiding Amounts
While ring signatures and stealth addresses hide sender and receiver identities, transaction amounts remain visible on most blockchains. Confidential Transactions (CT) address this gap by encrypting transaction amounts while still allowing network validators to verify that inputs equal outputs and no new coins are created.

Confidential transactions encrypt amounts while maintaining verifiability
Pedersen Commitments
The cryptographic foundation of Confidential Transactions is thePedersen commitment, a method of committing to a value without revealing it. These commitments have a special property called homomorphic addition—you can add commitments together and the result is a commitment to the sum of the values, all without ever revealing the individual amounts.
This property allows validators to verify that a transaction balances (inputs equal outputs) by checking that the commitments balance, without knowing the actual amounts involved. It's like verifying an equation is correct while all the numbers are hidden in sealed envelopes.
Range Proofs
A critical component of Confidential Transactions is the range proof, which prevents users from creating negative amounts or amounts exceeding the valid range. Without range proofs, someone could create a transaction with a negative output, effectively creating new coins out of thin air. Range proofs cryptographically demonstrate that committed amounts fall within valid ranges without revealing the actual values.
Recent innovations like Bulletproofs have dramatically reduced the size of range proofs, making Confidential Transactions more practical for blockchain implementation. Bulletproofs are non-interactive and don't require a trusted setup, making them an attractive option for privacy-preserving blockchain protocols.
Mixing and CoinJoin: Collaborative Privacy
Mixing services and CoinJoin protocols take a different approach to privacy by combining multiple users' transactions into a single transaction. This collaborative method breaks the direct link between inputs and outputs, making it difficult to trace the flow of funds.
CoinJoin Protocol
CoinJoin allows multiple users to combine their transactions into a single transaction with multiple inputs and outputs. When properly implemented, observers cannot determine which input corresponds to which output, providing privacy through ambiguity. Unlike centralized mixing services, CoinJoin is non-custodial—users never give up control of their funds.
Modern CoinJoin implementations use sophisticated coordination mechanisms to ensure privacy while preventing malicious participants from disrupting the process. Some protocols incorporate additional privacy features like equal-output amounts and multiple mixing rounds to enhance anonymity.
Advantages of Collaborative Privacy
- No trusted third parties required
- Works with existing blockchain infrastructure
- Privacy improves with more participants
- Can be combined with other privacy techniques
Layer 2 Privacy Solutions
Layer 2 scaling solutions offer new opportunities for privacy enhancement. By moving transactions off the main blockchain while maintaining security guarantees, Layer 2 protocols can implement privacy features that would be impractical on the base layer.
Layer 2 solutions enable enhanced privacy with improved scalability
Privacy-Preserving Payment Channels
Payment channels allow users to conduct multiple transactions off-chain, only settling the final state on the blockchain. This inherently provides privacy for intermediate transactions, as they never appear on the public ledger. Advanced payment channel networks can route payments through multiple hops, further obscuring the relationship between sender and receiver.
Zero-Knowledge Rollups
Zero-knowledge rollups combine the scaling benefits of Layer 2 with the privacy advantages of zero-knowledge proofs. These systems batch hundreds or thousands of transactions into a single proof that can be verified on the main blockchain. The proof confirms all transactions are valid without revealing individual transaction details, providing both privacy and scalability.
Challenges and Trade-offs
While privacy-preserving technologies offer significant benefits, they also introduce challenges that must be carefully considered. Understanding these trade-offs is essential for designing effective privacy solutions.
Performance and Scalability
Many privacy technologies require additional computational resources. Zero-knowledge proofs, while efficient to verify, can be computationally expensive to generate. Ring signatures increase transaction size proportionally to the ring size. These factors can impact blockchain throughput and increase transaction costs.
However, ongoing research continues to improve the efficiency of privacy technologies. Innovations like recursive proof composition and improved cryptographic primitives are making privacy more practical for mainstream blockchain applications.
Regulatory Considerations
Privacy-preserving technologies exist in a complex regulatory landscape. While privacy is a fundamental right, regulators worldwide are concerned about potential misuse for illicit activities. Blockchain projects implementing privacy features must navigate these concerns while protecting user rights.
Some projects are exploring selective disclosure mechanisms that allow users to prove compliance with regulations without sacrificing general privacy. These approaches aim to balance individual privacy rights with legitimate regulatory requirements.
Usability and Adoption
Privacy technologies often add complexity to user interactions. Generating zero-knowledge proofs, managing stealth addresses, or participating in CoinJoin rounds requires additional steps compared to standard transactions. Improving usability while maintaining strong privacy guarantees remains an ongoing challenge.
"The future of blockchain privacy lies not in choosing between transparency and confidentiality, but in giving users the tools to control what they reveal and to whom."
The Future of Blockchain Privacy
Privacy-preserving technologies continue to evolve rapidly, driven by both technological innovation and growing user demand for confidential transactions. Several trends are shaping the future of blockchain privacy.

Emerging technologies promise even stronger privacy guarantees
Programmable Privacy
Next-generation privacy systems are moving toward programmable privacy, where users can define custom privacy policies for different contexts. Smart contracts with built-in privacy features will enable complex applications while protecting sensitive data. This flexibility will be crucial for enterprise adoption of blockchain technology.
Cross-Chain Privacy
As blockchain ecosystems become increasingly interconnected, privacy must extend across chains. Cross-chain privacy protocols are being developed to maintain confidentiality even when assets move between different blockchain networks. These protocols will be essential for a truly decentralized and private financial system.
Quantum-Resistant Privacy
The potential advent of quantum computing poses a threat to current cryptographic systems. Privacy-preserving technologies are being designed with quantum resistance in mind, ensuring that confidential transactions remain secure even in a post-quantum world. Technologies like zk-STARKs and lattice-based cryptography are leading this effort.
Conclusion
Privacy-preserving technologies represent a critical evolution in blockchain development, addressing one of the most significant barriers to widespread adoption. Through innovations like zero-knowledge proofs, ring signatures, confidential transactions, and Layer 2 solutions, blockchain networks can provide strong privacy guarantees while maintaining the transparency and security that make decentralized systems valuable.
The path forward requires continued innovation in cryptography, careful consideration of regulatory requirements, and a commitment to usability. As these technologies mature, they will enable blockchain networks to serve a broader range of applications, from confidential business transactions to privacy-preserving identity systems.
The future of blockchain is not a choice between transparency and privacy, but rather a sophisticated balance where users control their information disclosure. Privacy-preserving technologies provide the tools to achieve this balance, ensuring that decentralized networks can serve the needs of individuals and organizations while respecting fundamental privacy rights.
As we continue to explore and refine these technologies, the blockchain ecosystem moves closer to realizing its full potential—a decentralized infrastructure that empowers users with both transparency and confidentiality, security and privacy, innovation and protection.