Consensus Mechanisms Explained: From Proof of Work to Modern Alternatives

The Foundation: What Are Consensus Mechanisms?
At the heart of every blockchain network lies a critical challenge: how do distributed nodes agree on the state of the ledger without trusting a central authority? Consensus mechanisms solve this fundamental problem by establishing protocols that enable network participants to validate transactions and maintain a single source of truth.
In traditional centralized systems, a single entity maintains the database and validates all transactions. Blockchain technology eliminates this single point of failure by distributing validation responsibilities across multiple independent nodes. However, this decentralized approach introduces complexity—nodes must coordinate to prevent double-spending, ensure data integrity, and resist malicious attacks.
Consensus mechanisms provide the rules and incentives that make this coordination possible. They determine who can add new blocks to the chain, how validators are selected, and what happens when nodes disagree. The choice of consensus mechanism profoundly impacts a blockchain's security model, transaction throughput, energy consumption, and degree of decentralization.
Proof of Work: The Original Consensus Protocol
Proof of Work (PoW) represents the pioneering consensus mechanism that powered the first blockchain network. Introduced in 2008, this protocol requires validators—called miners—to solve complex computational puzzles to earn the right to add new blocks to the chain.
How Proof of Work Functions
The PoW process begins when miners collect pending transactions into a candidate block. To validate this block, miners must find a specific number—called a nonce—that, when combined with the block data and passed through a cryptographic hash function, produces a result meeting predetermined difficulty criteria.
This computational work requires significant processing power and energy. The difficulty adjusts automatically to maintain consistent block production times, typically around 10 minutes for major networks. When a miner successfully solves the puzzle, they broadcast the solution to the network. Other nodes quickly verify the solution's validity and add the block to their copy of the blockchain.
Key Advantages of Proof of Work
- Battle-tested security:Over a decade of operation has proven PoW's resistance to attacks
- True decentralization:Anyone with computing resources can participate in mining
- Economic incentives:Mining rewards align validator interests with network security
- Objective validation:Mathematical proof makes consensus verification straightforward
The Energy Consumption Challenge
Despite its proven security, PoW faces significant criticism for its environmental impact. The computational race to solve cryptographic puzzles consumes enormous amounts of electricity. Major PoW networks can use as much energy as entire countries, raising sustainability concerns as blockchain adoption grows.
This energy intensity stems from PoW's fundamental design: security depends on making attacks prohibitively expensive through computational work. While this creates robust protection against malicious actors, it also means that as networks grow and become more valuable, energy consumption increases proportionally.

Proof of Stake: The Energy-Efficient Alternative
Proof of Stake (PoS) emerged as a response to PoW's energy consumption, replacing computational work with economic stake as the basis for validator selection. Instead of competing through processing power, validators lock up cryptocurrency as collateral to earn the right to propose and validate blocks.
Understanding Stake-Based Validation
In PoS systems, participants become validators by depositing a specified amount of cryptocurrency into a smart contract. This staked amount serves as a security deposit—validators who act maliciously risk losing their stake through a process called slashing. The network selects validators to propose new blocks based on factors including stake size, randomization, and time held.
When selected, a validator proposes a new block containing transactions. Other validators then attest to the block's validity. If the block receives sufficient attestations, it becomes part of the canonical chain. Validators earn rewards for honest participation, creating economic incentives that align with network security.
Proof of Stake Benefits
- Energy efficiency:Reduces energy consumption by over 99% compared to PoW
- Lower barriers to entry:Participants don't need specialized mining hardware
- Faster finality:Blocks can be confirmed more quickly than PoW systems
- Economic security:Attacking the network requires acquiring and risking significant stake
- Scalability potential:Opens pathways for sharding and other scaling solutions
Addressing Centralization Concerns
Critics of PoS point to potential centralization risks. Since validation power correlates with stake size, wealthy participants could theoretically accumulate disproportionate influence. This "rich get richer" dynamic differs from PoW, where mining power depends on ongoing operational costs rather than accumulated wealth.
However, modern PoS implementations include mechanisms to mitigate centralization. Delegation allows smaller holders to pool their stake while maintaining custody of their assets. Randomized validator selection prevents predictable patterns that could be exploited. Slashing penalties create strong disincentives against validator collusion or misbehavior.

Delegated Proof of Stake: Balancing Efficiency and Decentralization
Delegated Proof of Stake (DPoS) introduces a representative democracy model to blockchain consensus. Token holders vote to elect a limited number of delegates who take turns producing blocks. This approach prioritizes transaction throughput and efficiency while maintaining stakeholder governance.
The Delegate Election Process
In DPoS systems, token holders continuously vote for delegates using their stake as voting power. The top vote-getters—typically between 21 and 101 delegates depending on the network—become active block producers. These delegates rotate in a predetermined order, producing blocks at regular intervals.
Delegates earn rewards for block production and transaction fees. However, their position depends on maintaining community support. Token holders can change their votes at any time, creating accountability. Delegates who miss blocks, produce invalid blocks, or otherwise fail to serve the network risk losing their position.
DPoS Trade-offs
Advantages:
- High transaction throughput (thousands of transactions per second)
- Low latency and fast block confirmation times
- Energy efficient with minimal computational requirements
- Democratic governance through continuous voting
Challenges:
- Reduced decentralization with limited validator set
- Potential for vote buying or delegate cartels
- Voter apathy can concentrate power
- Trust assumptions around delegate behavior
Practical Byzantine Fault Tolerance and Its Variants
Practical Byzantine Fault Tolerance (PBFT) and its derivatives represent a different approach to consensus, drawing from decades of distributed systems research. These mechanisms prioritize finality and consistency, making them particularly suitable for permissioned blockchain networks and enterprise applications.
Byzantine Fault Tolerance Explained
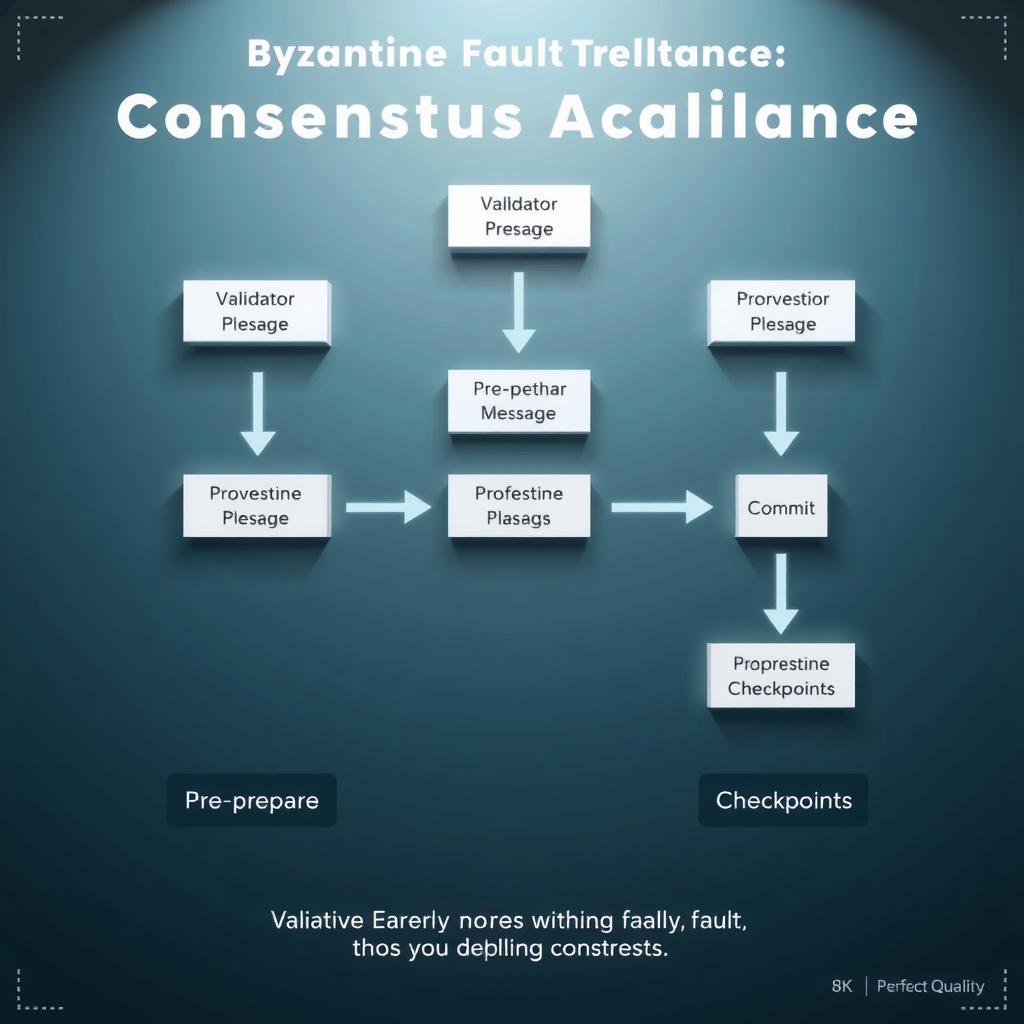
The Byzantine Generals Problem describes the challenge of achieving consensus in a distributed system where some participants may be faulty or malicious. PBFT solves this problem through a multi-phase voting protocol where validators exchange messages to agree on transaction ordering.
In PBFT, one validator acts as the primary and proposes a block. Other validators then go through pre-prepare, prepare, and commit phases, exchanging signed messages to verify agreement. Once a supermajority (typically two-thirds plus one) of validators commit to a block, it achieves finality—meaning it cannot be reversed.
Modern variants like Tendermint and HotStuff improve upon classical PBFT by reducing communication complexity and enabling better scalability. These mechanisms provide instant finality—once a block is committed, users can be certain their transactions won't be reversed, unlike probabilistic finality in PoW systems.
Emerging Consensus Innovations
The blockchain ecosystem continues to evolve, with researchers and developers exploring novel consensus mechanisms that address specific use cases and overcome limitations of existing approaches.
Proof of Authority
Proof of Authority (PoA) relies on pre-approved validators with established reputations. These validators stake their identity rather than cryptocurrency, making them accountable for their actions. PoA works well for private or consortium blockchains where participants are known and trusted, offering high throughput and energy efficiency at the cost of decentralization.
Proof of Space and Time
This mechanism uses storage capacity rather than computational power as the scarce resource for consensus. Validators prove they're dedicating disk space to the network over time. This approach reduces energy consumption compared to PoW while maintaining decentralization, though it introduces different hardware requirements and potential centralization vectors.
Proof of History
Proof of History creates a verifiable passage of time between events, allowing validators to process transactions in parallel without waiting for network-wide consensus on ordering. This innovation enables extremely high throughput while maintaining security, though it requires careful implementation to prevent timing attacks and ensure decentralization.
Hybrid Approaches
Many modern blockchain networks combine multiple consensus mechanisms to leverage their respective strengths. For example, some systems use PoW for initial block production but add PoS checkpoints for finality. Others employ different mechanisms for different layers of their architecture, optimizing for specific requirements at each level.
These hybrid approaches demonstrate that consensus mechanism design isn't binary—networks can thoughtfully combine techniques to achieve desired properties while managing trade-offs.
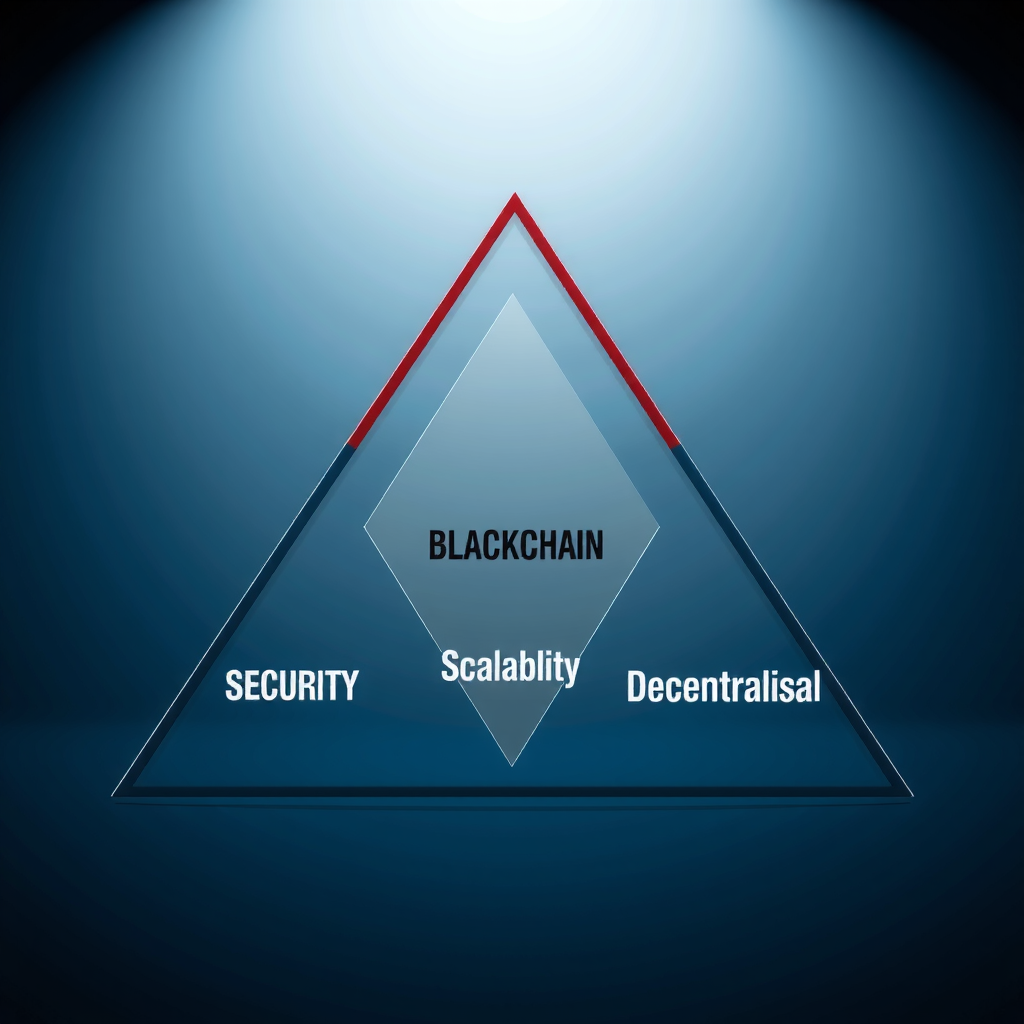
The Blockchain Trilemma: Security, Scalability, and Decentralization
Understanding consensus mechanisms requires grappling with the blockchain trilemma—the challenge of simultaneously optimizing for security, scalability, and decentralization. This framework helps explain why different networks make different consensus choices.
Security Considerations
Security in consensus mechanisms refers to resistance against attacks and the cost of compromising the network. PoW achieves security through computational expense—attacking the network requires controlling majority hash power, which becomes prohibitively expensive as the network grows. PoS achieves security through economic stake—attackers must acquire and risk significant capital.
Different mechanisms face different attack vectors. PoW networks must defend against 51% attacks where an attacker controls majority mining power. PoS networks must prevent long-range attacks where validators with historical stake attempt to rewrite history. BFT-based systems must ensure that fewer than one-third of validators are malicious.
Scalability Trade-offs
Scalability measures a network's transaction throughput and ability to handle growing demand. PoW systems typically process fewer transactions per second due to block time and size constraints. DPoS and BFT-based systems can achieve much higher throughput by limiting the validator set and optimizing communication protocols.
However, higher throughput often comes with trade-offs. Faster block times can increase the rate of temporary forks. Larger blocks require more bandwidth and storage, potentially excluding participants with limited resources. These factors affect decentralization and security.
Decentralization Dynamics
Decentralization encompasses both the number of validators and the distribution of power among them. PoW theoretically allows anyone to mine, but in practice, mining has concentrated in pools and regions with cheap electricity. PoS can be more accessible since it doesn't require specialized hardware, but wealth concentration can lead to validator centralization. DPoS explicitly limits validators but uses voting to maintain accountability.
Choosing the Right Consensus Mechanism
No single consensus mechanism is universally superior—the optimal choice depends on specific use case requirements, priorities, and constraints. Understanding these factors helps explain why different blockchain networks make different design decisions.
Public vs. Permissioned Networks
Public blockchains prioritize censorship resistance and permissionless participation, making PoW and PoS natural choices despite their complexity. Permissioned networks where participants are known can use more efficient mechanisms like PBFT or PoA, sacrificing some decentralization for higher performance and lower costs.
Performance Requirements
Applications requiring high transaction throughput and low latency—such as payment systems or decentralized exchanges—benefit from mechanisms like DPoS or optimized BFT variants. Applications where security and immutability are paramount—such as digital gold or long-term record keeping—may accept lower throughput in exchange for battle-tested security.
Environmental Considerations
As sustainability becomes increasingly important, energy consumption weighs heavily in consensus mechanism selection. PoS and its variants offer dramatic energy savings compared to PoW, making them attractive for environmentally conscious projects and jurisdictions with strict energy regulations.
Decision Framework
When evaluating consensus mechanisms, consider:
- Security model:What attacks must the network resist? What's the cost of compromise?
- Performance needs:What throughput and latency does the application require?
- Decentralization goals:How important is permissionless participation?
- Resource constraints:What are the energy, hardware, and bandwidth limitations?
- Governance preferences:How should protocol changes be decided?
- Regulatory environment:What compliance requirements must be met?
The Future of Consensus Mechanisms
Consensus mechanism research remains an active and evolving field. As blockchain technology matures and new use cases emerge, we can expect continued innovation in how distributed networks achieve agreement.
Layer 2 Solutions and Consensus
Layer 2 scaling solutions introduce new consensus considerations. State channels, rollups, and sidechains can use different consensus mechanisms than their base layer, optimizing for specific requirements. This layered approach allows networks to achieve properties that would be difficult to obtain with a single consensus mechanism.
Cross-Chain Consensus
As blockchain ecosystems become more interconnected, consensus mechanisms must evolve to support secure cross-chain communication. Bridge protocols, atomic swaps, and interoperability layers require new approaches to achieving consensus across networks with different security models and trust assumptions.
Quantum Resistance
The potential advent of quantum computing poses challenges for current consensus mechanisms that rely on cryptographic assumptions. Research into quantum-resistant consensus protocols ensures blockchain networks can maintain security as computing technology advances.
Future consensus mechanisms will likely incorporate post-quantum cryptography, new economic incentive structures, and novel approaches to achieving Byzantine fault tolerance in increasingly complex distributed systems.
Key Takeaways
- Consensus mechanisms enable decentralized networks to agree on state without central authority
- Proof of Work provides proven security but consumes significant energy
- Proof of Stake offers energy efficiency and new scaling possibilities
- Alternative mechanisms like DPoS and BFT variants optimize for specific use cases
- The blockchain trilemma explains trade-offs between security, scalability, and decentralization
- No single consensus mechanism is universally optimal—choice depends on requirements
- Ongoing innovation continues to expand the possibilities for distributed consensus
Conclusion
Consensus mechanisms represent one of blockchain technology's most fundamental innovations—the ability to achieve agreement in trustless, distributed environments. From the pioneering Proof of Work to modern alternatives like Proof of Stake and beyond, each mechanism offers different trade-offs in security, performance, and decentralization.
Understanding these mechanisms is essential for anyone working with or evaluating blockchain technology. The choice of consensus protocol profoundly impacts a network's characteristics, from its energy consumption and transaction throughput to its security model and governance structure.
As the blockchain ecosystem continues to mature, we can expect further innovation in consensus mechanisms. New approaches will emerge to address specific use cases, overcome current limitations, and enable applications that aren't possible with today's technology. The evolution from Proof of Work to modern alternatives demonstrates the field's dynamism and the ongoing quest to build more efficient, secure, and scalable decentralized systems.
Whether you're a developer choosing a platform, an investor evaluating projects, or simply someone interested in blockchain technology, understanding consensus mechanisms provides crucial insight into how these revolutionary systems actually work—and where they might be heading next.